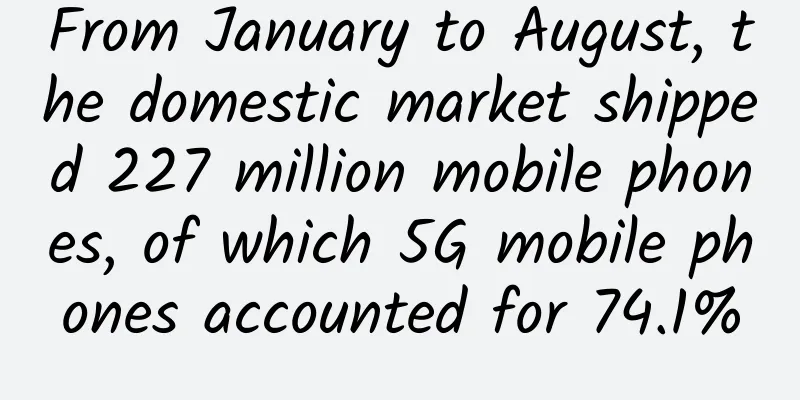How can Internet + smart hardware save your privacy?

|
In recent years, with the popularization of the Internet, various network security incidents related to the leakage of user privacy have occurred frequently. The rise of the "Internet +" wave has, in a sense, pushed this problem to the previously relatively safe hardware field. How do smart hardware expose your privacy? There are many hardware manufacturers that have been accused by consumers of privacy issues, including technology giants such as Google, Apple, and Amazon. Relevant data shows that by the end of last year, nearly 109 million wearable devices were in use worldwide. Smart products that have gradually penetrated into every corner have made the theft of user privacy information more covert. Recently, a live streaming website called "An Qiao Qiao" has sparked heated discussions. Its video content includes relatively private home life scenes. Some of these videos come from smart cameras originally used for home security monitoring. In many cases, users are not aware that these products pose a threat to personal privacy. In fact, when the following scenarios occur in life, it is necessary to reflexively consider your privacy issues. Scene 1: Photographing and recording The privacy protection of the first generation of Google Glass has been widely controversial. Some users used Google Glass to secretly film private conversations, which led to some places banning Google Glass. Foreign media even coined the term "glasshole" to satirize the product, which was recognized by the public. This can be regarded as the first time that the security issues of smart products have attracted public attention. Ultimately, Google's first generation of glasses withdrew from the stage under heavy pressure, but similar privacy protection issues have only increased. Information leakage in the form of video can be said to be the most embarrassing scenario, especially when the video involves private places. Therefore, when various types of cameras such as computers, mobile phones, and tablets flash inexplicably or someone wearing glasses with "small eyes" devices is pointing at you, pay attention to your privacy. Scenario 2: Voice Recognition Voice control technology is becoming a standard feature of more and more smart devices, from watches and mobile phones to speakers, TVs and even children's toys. The introduction of smart voice assistants has freed users' hands and, to a certain extent, filled the special emotional needs of some modern people; on the other hand, its "real-time standby" feature has also added more security risks. For example, Apple's latest Hey Siri wake-up function. In theory, the device is always comparing the audio data in the environment. For hackers, this is a rare entry point for monitoring or recording. Amazon's smart assistant speaker Echo has caused dissatisfaction among consumers due to privacy issues, which is one of the reasons why Google is a little cautious in the field of smart homes. Scenario 3 Wearable Devices Yesterday, there was a news report that a netizen used a bracelet to record the various parameters of the "private movements" between himself and his partner, and uploaded the screenshots to the Internet, which caused heated discussion for a while. In addition to exercise parameters, the bracelet may also expose your location and status. Experts say that data transmission between smart devices and mobile phones via Bluetooth is not secure and may be intercepted and decoded by attackers. Wearable devices are in close contact with the human body for a long time, which gives them an inherent advantage in collecting health data. At the same time, they also put forward higher requirements for user privacy protection. Apple Watch was questioned by the Attorney General of Connecticut for this issue. Even if hackers are not interested in this part of the data, whether the device manufacturer will sell it to a third party without the user's authorization is also a question that needs to be considered. The FTC has shown a strong interest in the Apple Watch and its function of tracking the wearer's pulse. Scenario 4: Various types of encryption Generally speaking, encryption is a layer of protection for personal information, so why do we need to pay special attention when it comes to encryption scenarios? The devil is always stronger than the righteous. In recent years, from symbol passwords to fingerprints, faces, voices, irises and other biometric passwords, every breakthrough in encryption technology is accompanied by a series of upgrades in cracking technology. At some point, passwords only serve as a marker of valuable information for hackers, and users are more likely to take these encrypted information lightly. In addition, password input is a scenario that requires a higher level of privacy awareness, especially when using hardware to make payments in public places. From the above scenarios, we can see that networking, as a major feature of intelligence, has brought hardware products from a relatively closed, independent localized environment to a more open and complex network environment, and risks and security risks have also come along. The simplification of visual and audio input devices and the popularization of various sensors have made it possible to collect real-time and reliable data. Smart hardware is becoming a major data entry point in the upcoming big data era. These data may bring unprecedented convenience to people's lives, but once leaked, their destructive power will be beyond your imagination. The crisis after privacy leakage Professionals revealed that by fine-grained positioning analysis of the movements of the smart bracelet, attackers can know which button you are tapping. This means that it is at least technically feasible to hack into your bank account by cracking your password. The aforementioned obscene video circulation is only one of the hazards caused by the hacking of smart cameras. So far, it has not caused direct economic losses to users. There are cases showing that hackers can bypass the owner's surveillance by locking dynamic videos and then break into the house to commit crimes. Of course, the circulation of some videos may directly endanger the stability and harmony of the family. In addition to exposing health or exercise, wearable devices may even cause more serious harm. For example, after being controlled by hackers, the bracelet can monitor the user's sleep depth and help criminals determine the timing of the crime. For advertisers, content and service providers, the information such as user habits hidden behind the data has more attractive commercial value. This also provides device manufacturers with data with an opportunity to directly monetize the data. Therefore, the protection of privacy data is probably far from enough just by improving user security awareness. The standardization of privacy policies, the upgrading of security technologies and the self-discipline of device manufacturers are also very important. As a winner of Toutiao's Qingyun Plan and Baijiahao's Bai+ Plan, the 2019 Baidu Digital Author of the Year, the Baijiahao's Most Popular Author in the Technology Field, the 2019 Sogou Technology and Culture Author, and the 2021 Baijiahao Quarterly Influential Creator, he has won many awards, including the 2013 Sohu Best Industry Media Person, the 2015 China New Media Entrepreneurship Competition Beijing Third Place, the 2015 Guangmang Experience Award, the 2015 China New Media Entrepreneurship Competition Finals Third Place, and the 2018 Baidu Dynamic Annual Powerful Celebrity. |
>>: Qualcomm: European 5G Action Plan Evaluation Report
Recommend
This is the correct way to clean up WeChat storage space. No wonder others can clean up several GB.
A few days ago, a fan left a message saying that ...
How to use online traffic to sell goods?
1. The key to the current counter-trend growth: u...
The "White Dragon" horse that jumped into the river to save people died. Why do people always say "an ox is made of iron, but a horse is made of paper"?
Produced by: Science Popularization China Author:...
A complete guide to event operations! A must-see for operators!
Event operation is a job that most operations per...
Introduction to OPPO App Store Information Stream Ads
FAQ - Information Stream Advertising Advertising ...
The sound of an inflatable lifelike doll. Does the inflatable doll sound nice?
An inflatable doll, as the name suggests, is an i...
Are you worried about not being able to write about the advantages of your product in an interesting way? Use these two tricks, customers will be itchy as soon as they read it
This article is going to talk about copywriting ,...
Random talk: "Zhejiang" scientist Qian Xuesen: If you fail the times, how can you have a good time?
...
Across a century, we meet the "Chinese Marie Curie"
[Popular Science Long Picture] Across a Century, ...
More than half of people don't know they have diabetes! Be alert if you have these symptoms
World Diabetes Day is celebrated on November 14th...
Tips and strategies for placing Weibo Fans Advertising!
The eyewear industry has reached a historical jun...
The trend of "Four Uncles" playing with skewers has spread to children! Will primary school students get tenosynovitis from playing with skewers?
When it comes to playing with bracelets, the firs...
Octopus has parasites?! Octopus: That's my partner's penis...
In 1829, Georges Cuvier, a leading figure in the ...
The external form and underlying logic of event promotion!
Why build event marketing tools? What is the purp...
Are there any Google agents in Shantou who would like to find them to help with promotion?
Guangdong Jimifeng is Google's agent in Guang...